About
Category
Cyber Security , Network Security ,
A cutting-edge network monitoring solution designed to help organizations of all sizes and complexities to monitor their networks with accuracy, speed, and effectiveness. It is built on machine learning algorithms, data mining techniques, and threat intelligence capabilities, which allow organizations to detect even the most sophisticated and previously unknown threats.
With this solution, organizations can be confident that they have the tools they need to protect their networks and respond quickly and effectively to any threats they encounter.
Team Members
5
Weeks to launch MVP
7
Months of Project delivery time
6
The Challenge
- Migration from Angular to React development using Carbon Design System.
- Implementation of libraries and AngularJS features in ReactJS.
- Challenges with front-end data management (searching, sorting, pagination, column hiding/showing and reordering) without back-end API support.
- Handling large and raw data responses from back-end APIs.
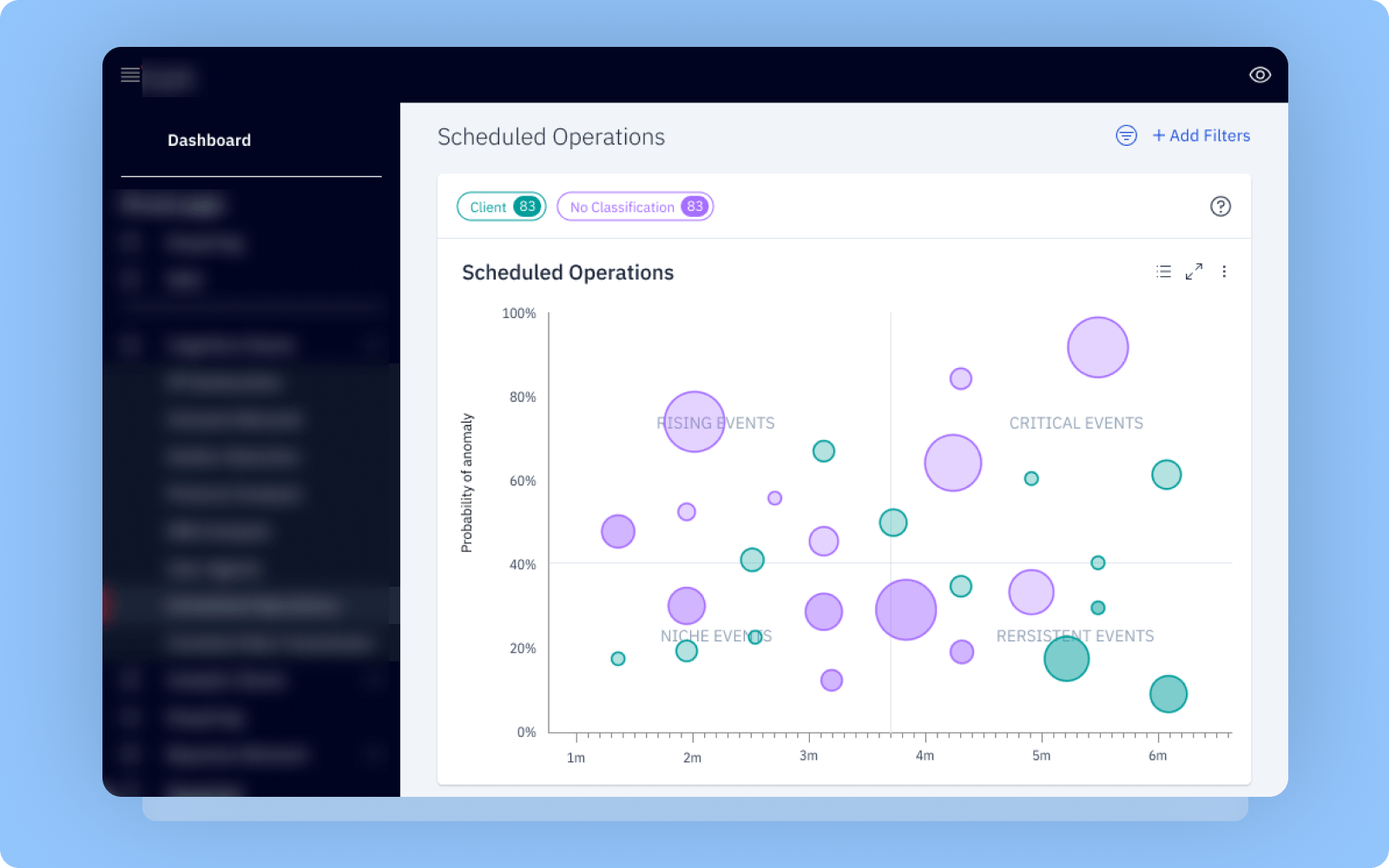
- Complex implementation of various networking and GForce-node charts and reports (13 charts such as donut chart, bar chart, heat map, scatter chart, bubble chart, bubble plot chart, intranetwork chart, etc.).
- Parent-child hierarchical table structure with context-based navigation and field properties.
- Group by mode in table and customization of table fields for producing new tables from a list.
The Solution
- Successfully done React development using Carbon Design System and implemented necessary libraries and Angular features in ReactJS.
- Adopted the common component-based architecture to manage the table and grid structure for parent-child table hierarchy, including global implementation of table and table actions (such as sorting, searching, pagination, and column reordering)
- Efficiently handled the large data in the front-end by mapping and keywising the data to produce meaningful responses.
- Applied the ANT and Carbon charts, icons, and classes for styling components
- Created a user-configurable table structure, allowing users to customize their fields and produce new table combinations with common features such as searching, sorting, column reordering, and column hiding/showing.
Key features
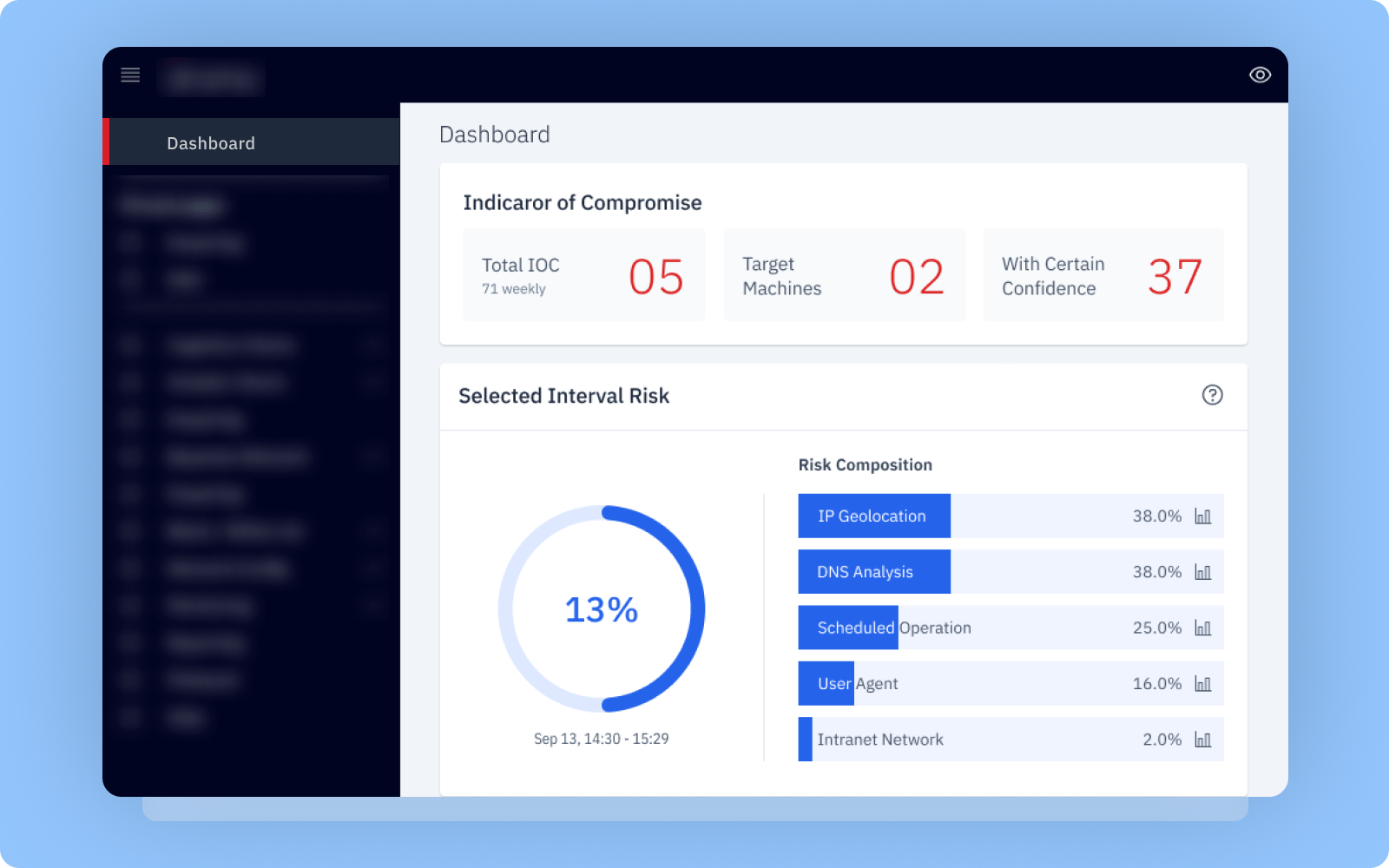
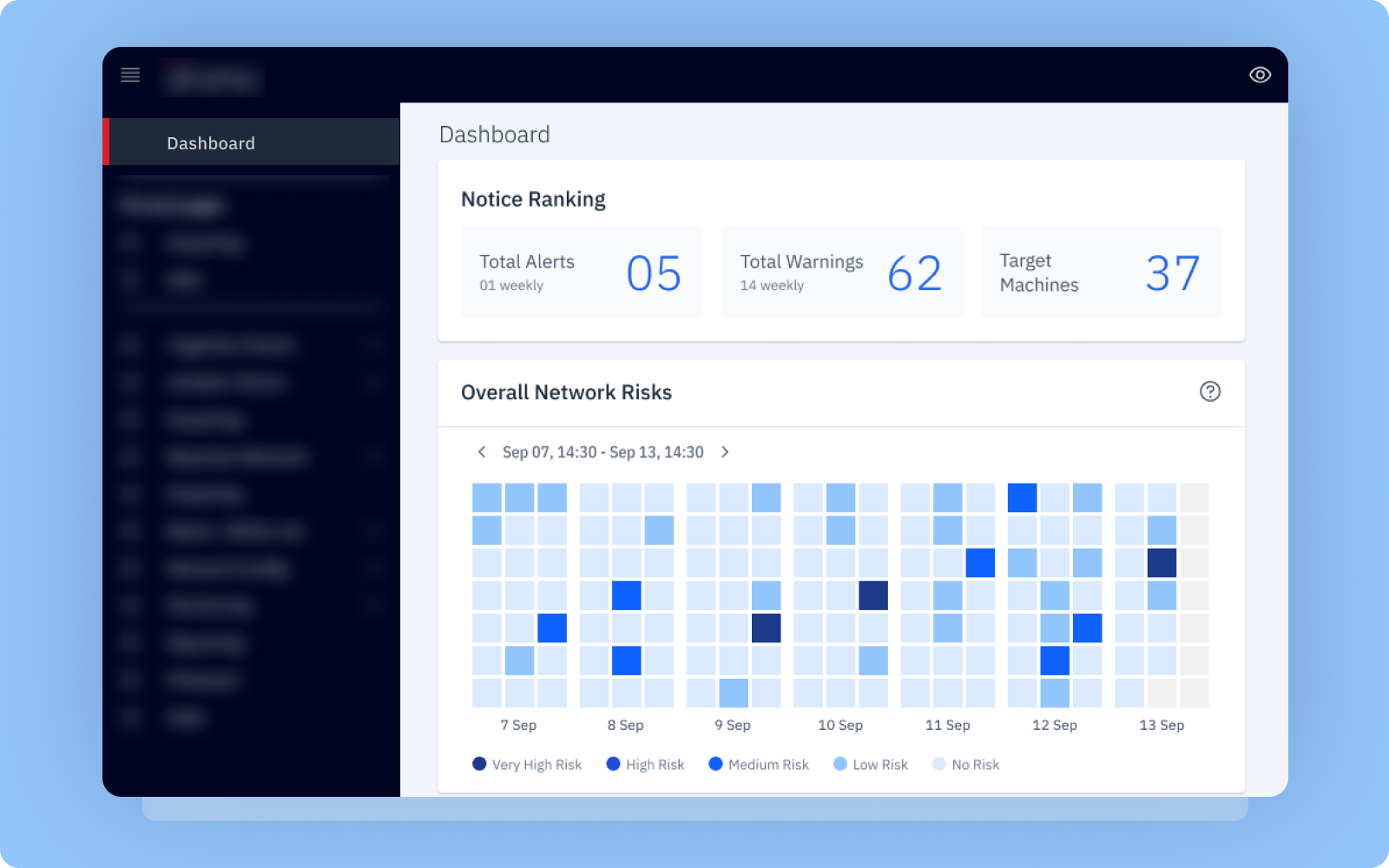
- Alerts and warnings for targeted machines
- Identification of network risks and suspicious machines
- Assessment of machine risks
- Cognitive and analytic charts for data visualization
- Black and white IP list, categorized by country and domain
- Network topology mapping and services information
Results
- Feature-rich dashboard with intuitive user interface
- Reduces efforts to reach at the huge and complex networking data per second
- Better decision making with the help of analytical charts
- Greater frontend control and customization
Facts
& Figures
- X number of mathematical models used by AI
Tech stacks we used
We used a variety of cutting-edge technologies and frameworks to develop a robust security risk assessment system, including:
Technologies
ReactJS
Libraries
Carbon Design System, Carbon Library, ANT Library
Frameworks
React.js, Vite.js
Tools and Utilities
React hooks, Yarn, Eslint, Tailwind CSS
Packages
Axios, Recoil, Tanstack React query, Lodash
Have a look at
Our success stories
Over the years, Peerbits have delivered several customized solutions to their clients across the globe. You can get a closer look at few of such success stories here.