Did you know that 91% of organizations admit that security slows down their pipeline? It’s a staggering number, but if you’ve ever lived through a last-minute security check before a release, it probably doesn’t surprise you.
Usually DevOps is built for speed giving quick releases, fast feedback, continuous updates. But when security gets added on at the end, the whole team holds its breath: will the build pass, or will they have to start over? For developers, it’s frustrating gates; for operations, its compliance delays & for leadership, its missed deadlines and rising costs.
To counter instead of ripping code apart during a last-minute review, DevSecOps is used to build a secure CI/CD workflow from the ground up. With DevSecOps security is integrated at every stage of the software lifecycle helping companies fasten the devops workflows.
Still the problem doesn’t end here.
If you’ve just switched to DevOps services and found it slowing you down instead of fastening your deployments, or if you’re already facing DevSecOps pipeline issues, this blog is for you.
Here you will get to know why security still breaks pipelines, show you how to identify issues, and give you expert-verified DevSecOps pipeline best practices in 2025 to transform your CI/CD pipeline security.
First, let’s start by understanding why pipelines slow down with security integration in the first place.
Why does security break DevOps pipelines?
Even in 2025, security remains one of the biggest friction points in DevOps workflows. Here’s why:
1. Legacy practices creeping in
Too many organizations still treat security like a post-deployment audit rather than a proactive step. Vulnerability scans run only after code is deployed into staging or production, which means teams find problems when it’s already too late. The only fix remaining is a painful cycle of rewrites and delays.
2. Tool Sprawl
Modern enterprises often rely on multiple scanners: one for code, another for dependencies, another for containers, and yet another for cloud compliance. This leads to security pipeline failures caused by tools that don’t communicate. Instead of streamlining, the toolchain gets stuck and creates duplicate check points.
3. Compliance Overhead
Regulators demand strict checks but most companies still handle these manually even in 2025. Compliance reviews add weeks to releases, when they could have been automated through policy-as-code frameworks.
4. Cultural Friction
The toughest challenge isn’t technical, it’s cultural. Developers prioritize speed. Security teams prioritize protection. Operations prioritize uptime. When their KPIs conflict, security becomes a major issue instead of a shared responsibility.
Personal Insight: “I’ve seen teams spend three weeks fixing what could’ve been caught in a three-minute static scan if wired correctly. For many organizations, even spotting the problem is the hardest part.”So how do you recognize that these issues are affecting your own pipeline? Let’s break that down.
How to spot issues in your CI/CD pipeline?
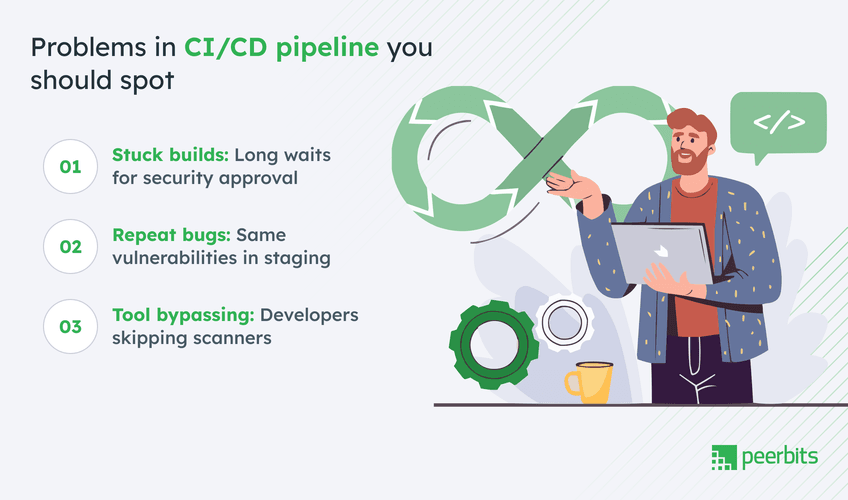
Identifying problems early is the first step toward fixing them. Here are the most common red flags to spot in your CI/CD pipeline:
- Builds stuck in the security review queue. If your builds constantly sit waiting for approval, that’s a signal of inefficient security automation in CI/CD.
- Repeated vulnerabilities in staging. If the same issues are popping up late in the process, it means security isn’t embedded early enough.
- Developers bypassing tools. If devs are disabling scanners or skipping security steps because they are slowing down the feedback loops, you’ve got a big problem.
These indicators highlight pipeline security mistakes that cripple performance. To solve them, you need smarter strategies built around DevSecOps best practices.
Read more: Difference between DevOps vs DevSecOps
Best DevSecOps pipeline fixing best practises in 2025
DevSecOps is a methodology that integrates security directly into your DevOps pipelines. Instead of treating security as an afterthought, it’s included security into every stage from writing code to deploying apps.
Here’s how to apply DevSecOps best practices to solve real-world slowdowns:
1. Shift-Left security with context-aware tools
Integrate static code analysis tools like Snyk or GitHub Advanced Security into your developer workflows. This guarantees vulnerabilities are caught the moment code is written, not weeks later. Developers get instant feedback, and you save time downstream.
2. Automated gates. Not walls
Don’t let security become a hard blocker. Instead, design soft fail gates: during development, issues flag as warnings; during release candidates, they become hard failures. With this your dedicated team for hire keeps moving fast while keeping secure CI/CD workflows.
3. Compliance as code
Tools like Open Policy Agent (OPA) and Terraform Sentinel can automate compliance checks. Instead of long manual review boards, you ca define security policies as code, making sure every build is automatically compliant.
4. Toolchain consolidation
Rather than adding more tools, consolidate with orchestration platforms like Prisma Cloud or Aqua Security. A smaller, smarter toolchain cuts latency and improves collaboration.
5. Cultural shift
The most important fix? Make security a shared KPI across dev, sec, and ops. When everyone is accountable, no team feels like the bottleneck.
With these strategies, you can build a secure CI/CD workflow without sacrificing velocity. But let’s go deeper. Here are some insider hacks most teams don’t know.
Insider hacks to fix DevOps pipeline (that noone tell)
Since you’ve made it this far, it’s time to share the pro-level DevSecOps pipeline best practices that don’t always make it into glossy playbooks. But I am sure, they can save you weeks of frustration (and plenty of developer goodwill).
-
Never put DAST in your main CI/CD loop.
Dynamic Application Security Testing (DAST) is resource-heavy and slow by nature. Running it inline with every commit will grind your pipeline to a halt. Instead, you can schedule DAST scans in parallel environments or as part of nightly builds. This way, you still catch runtime issues early, without choking your release velocity.
-
Don’t run full security suites on every commit.
Security checks need to be risk-based, not blanket rules. If you get a small pull request for a typo fix? Run lightweight static analysis only. Only when something major commits touches critical modules, does it trigger the full suite. This tiered approach makes sure you’re not wasting cycles scanning non-critical changes while still protecting the crown jewels.
-
Secrets management is where pipelines choke.
This is one of the biggest hidden slowdowns in modern pipelines. When developers wait for manual vault approvals or struggle with rotating keys, that’s when productivity collapses. Instead, adopt automated secret rotation policies integrated into your DevSecOps toolchain.
-
Pipeline latency must be monitored religiously.
This one’s non-negotiable. If security adds more than 10% latency to your builds, developers will start looking for shortcuts or bypasses. This creates new vulnerabilities. Track and measure your pipeline latency at every stage. Treat speed as a KPI alongside security so you can maintain balance.
-
Pro Hack: Build a “canary pipeline.”
Before rolling out new security tools across your org, test them on a smaller branch or project pipeline. Measure the latency, bug detection rate, and developer feedback. Then, scale only what works for your company. This avoids the “tool shock” effect where an entire organisation suddenly gets stuck with an over-engineered security tool.
-
Automate context-aware reporting.
Raw issue dumps overwhelm teams. Instead, assess your scanners to provide developer-ready, context-rich feedback. A report that says “SQL Injection risk detected in file X, line 243, introduced in PR #57” is infinitely more actionable than a generic “high severity issue found.”
These are the small but powerful DevSecOps challenges that most blogs don’t mention, yet they make all the difference in practice. To maintain them for the long term try using the following tools for fixing.
Tools for pipeline fixing with DevSecOps in 2025
Now, let’s talk about tools. The future of DevSecOps is lightweight, developer-first solutions that integrate seamlessly with CI/CD. Here’s a quick insight on tools to use for fixing pipeline slowdowns:
- Snyk
Best for: Open-source vulnerabilities. Scans dependencies in real time, flags known risks, and even suggests fixes for keeping your open-source stack secure without slowing development.
- GitHub Advanced Security
Best for: Security built into workflows. This tool offers static code analysis, secret scanning, and dependency checks right inside GitHub, catching issues early with minimal friction.
- Prisma Cloud
Best for: Compliance and cloud-native security. This pipeline fixing tool secures workloads, IaC, and multi-cloud environments while automating compliance checks. This makes it ideal for enterprises under regulation.
- Aqua Security
Best for: Container and runtime protection. This tool goes beyond image scanning with runtime defenses and policy enforcement built for Kubernetes and microservices pipelines.
Best for: All-in-one developer-first security. Scans code, dependencies, containers, and cloud infrastructure in one unified platform, prioritizes real risks, and integrates directly into CI/CD pipelines to keep releases secure without slowing development.
Personal insights: “I’ve phased out four different vulnerability scanners for clients and cut pipeline runtime by 40%; that too just by consolidating with integrated tools.”Wait…wait..don’t just jump onto new tools without an action plan. The best DevSecOps implementation comes from aligning tools with workflow strategy.
Action plan for business owners & tech leads
If you’re serious about fixing your pipeline, here’s a short and easy step-by-step action plan:
1. Audit your pipeline
Spot hidden security issues.
2. Decide what to automate vs what to gate
Automate low-risk checks, gate only high-risk ones.
3. Consolidate your toolchain
Use fewer but smarter tools to keep it simple & focused.
4. Track pipeline metrics
Monitor latency, automation percentage, and mean time to remediate.
5. Align security with KPIs
Make it everyone’s responsibility, not just the SecOps team’s to keep track on security.
This is how enterprises move past pipeline security mistakes and build resilient workflows that scale.
Conclusion
As understood so far, the myth that “security slows pipelines” is outdated. With the right DevSecOps strategy, you can transform security from a pipeline breaker into a pipeline accelerator.
In 2025, organizations that adopt DevSecOps pipeline best practices are able to achieve faster release cycles, fewer vulnerabilities, and less friction between teams. This translates to the future of DevSecOps, which is not about choosing between speed and security. It is significant to achieve both.
The companies going ahead with the DevSecOps approach not only ship software faster, but also build trust with customers, meet compliance requirements effortlessly, and reduce the long-term costs of fixing security flaws late in the game. Simply put, with the right set of DevSecOps your company can reach the ultimate competitive edge no matter the technology or compliance updates.
Talk to a Peerbit’s DevSecOps expert.
Get expert guidance to speed up your DevOps pipeline while staying fully secure & compliant.
Let’s talkFAQs
DevSecOps integrates security into every stage of the DevOps pipeline, guaranteeing that speed and innovation aren’t sacrificed for safety.
Monitoring pipeline logs, tracking failure points, and analyzing feedback loops can reveal where security is causing delays.
Shift-left security, automated gates, compliance as code, toolchain consolidation, and shared KPIs across teams.
The best hack is to run DAST in parallel, use risk-based triggers, automate secrets rotation, and monitor latency closely.
AI-assisted testing, predictive risk analysis, and cloud-native security tools are making DevSecOps faster, smarter, and more integrated than ever.